The Easiest Way to Achieve Zero Trust Access Management in the Cloud
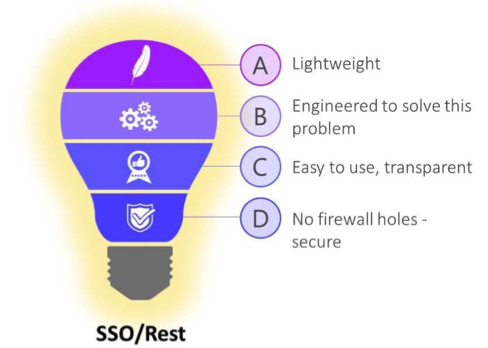 SSO/Rest provides your enterprise with a lightweight, transparent way to deploy your applications to the Cloud while still protecting them with the full power and capabilities of your existing Web Access Management (WAM) platform. Crucially, SSO/Rest delivers Zero Trust Access Management, ensuring that every request gets vetted before ever touching your applications or resources.
SSO/Rest provides your enterprise with a lightweight, transparent way to deploy your applications to the Cloud while still protecting them with the full power and capabilities of your existing Web Access Management (WAM) platform. Crucially, SSO/Rest delivers Zero Trust Access Management, ensuring that every request gets vetted before ever touching your applications or resources.
If your organization has yet to implement an enterprise WAM solution, is running pre-Cloud WAM, or uses Cloud IDM, then SSO/Rest provides a flexible, powerful, and vendor-independent way to fully secure your resources.
SSO/Rest is a CA Technologies TTP Validated Solution.
Read more: SSO/Rest – One Product, Four Solutions
How It Works
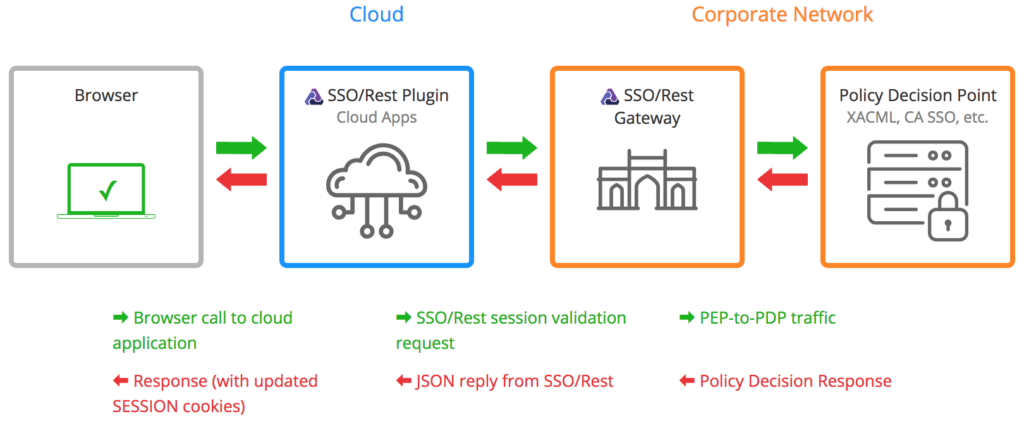
SSO/Rest was built to solve the central problem plaguing enterprises that wish to extend the protection of their WAM solutions to the Cloud: that all pre-Cloud SSO products depend on agents or proxies that work poorly in the Cloud – both because of their “heaviness” and their reliance on vendor proprietary communication protocols.
Instead, lightweight, HTTP-speaking “plugins” replace bulky, resource-intensive web agents:- Small footprint and self-contained.
- No chatty, proprietary protocols minimize latency and no new firewall holes.
- No cryptographic operations means low processor-burden and less patching.
- Can be drop-replace deployed on applications both inside and outside the enterprise perimeter.
- Communicates with the plugins via REST-compliant web services.
- Securely mediates communication between the plugins and Policy Decision Points (e.g. CA SSO Policy Servers).
- Handles the resource-intensive crypto.
Sign On
Together, the plugins and the SSO/Rest Gateway create a virtual perimeter, safely providing full WAM to all your critical resources, whether they reside in your data center or have been deployed to the Cloud. By extending true WAM (as opposed to the more limited functionality provided by federation), SSO/Rest provides not only authentication and Single Sign On but also:
- Session Management – both session duration control and idle session timeouts;
- Centralized Audit; and
- Zero Trust Access Management – the plugins enforce your centralized access control policies to ensure that every request gets vetted before ever touching your applications or resources.
SSO/Rest can be used in conjunction with all major enterprise WAM platforms, but can also run as a fully functional, stand-alone WAM solution.
Where SSO/Rest resides
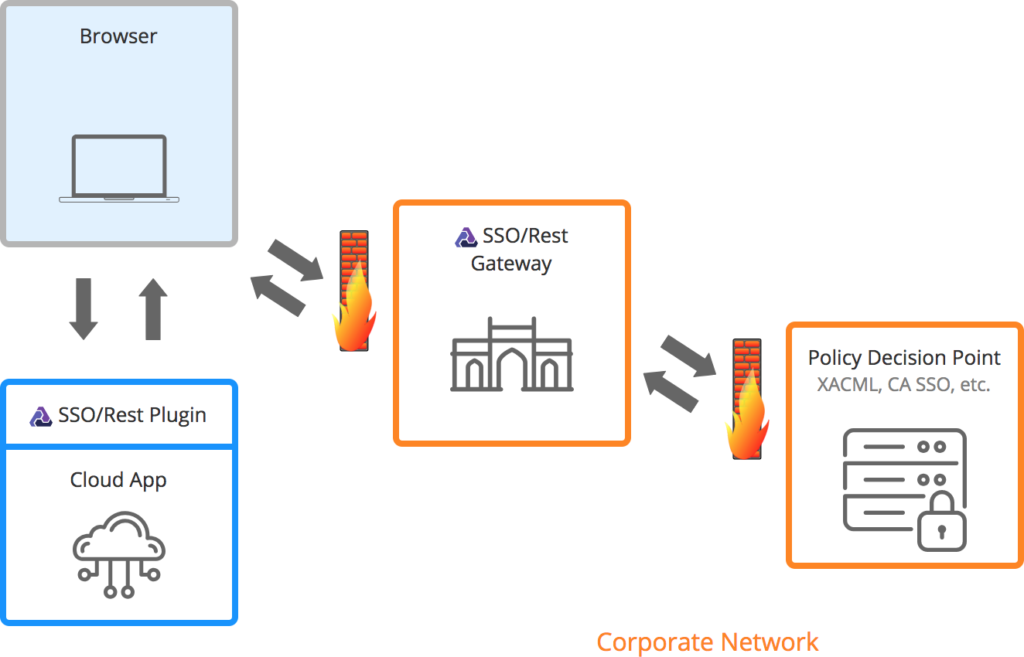
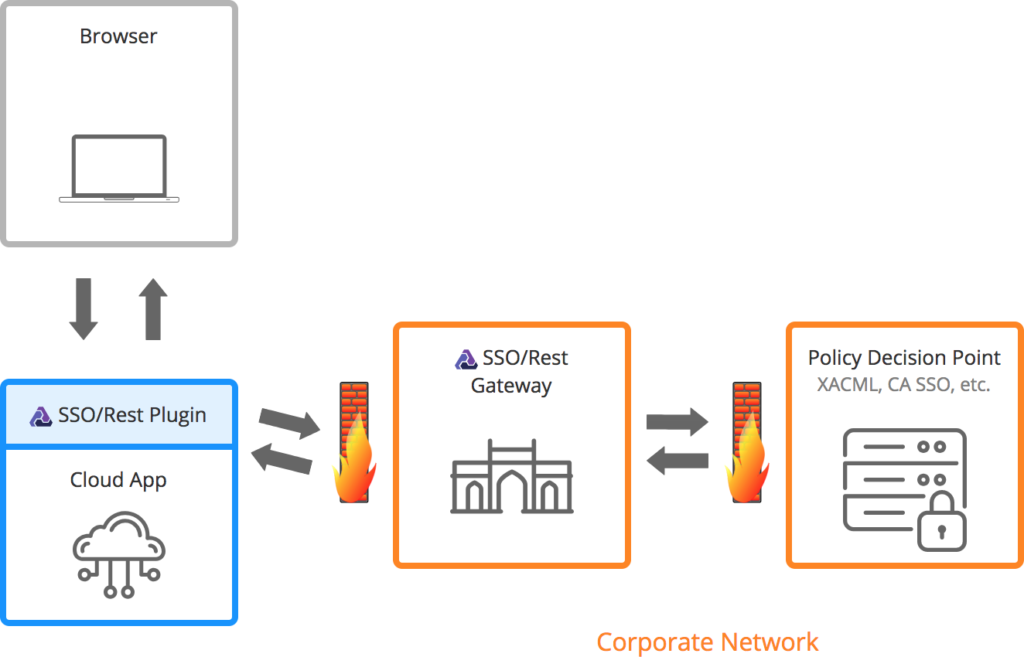
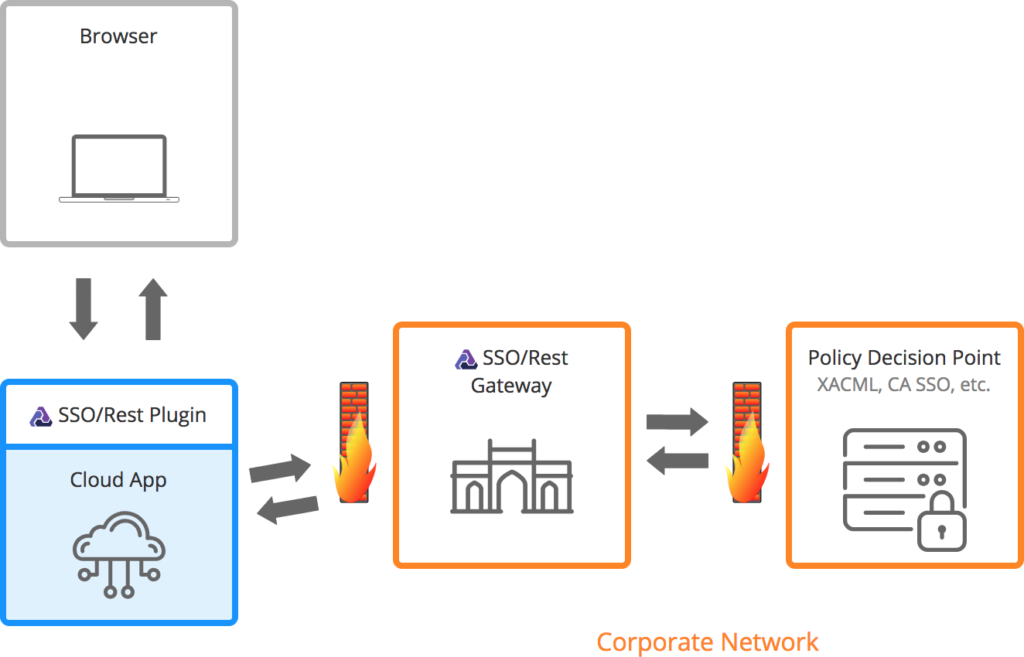
SSO/Rest Plugin Architecture
SSO/Rest Plugin Architecture
Flexible infrastructure, using standards-based components and technologies
Enforces session management rules and timeouts across all applications, whether on-site or cloud-based
End-to-end identity propagation and session (re)validation
Powerful logging, monitoring, tuning and global cache management
Kibana-powered dashboard for OOTB health and performance monitoring
General
Web servers: Apache HTTP Server, Microsoft IIS, NGINX
J2EE containers: IBM WebSphere, Red Hat WildFly (JBoss), Apache Tomcat, and Oracle WebLogic
Cloud platforms: Amazon AWS, Microsoft Azure and Google Cloud
Deployment: a preconfigured Tomcat zip distribution, a VM appliance, or a Docker image
Use with: AJAX, Mobile or native applications
Access policies: XACML-based policy engine or within your existing legacy SSO solution
Platforms
Pluggable gateway logic for flexible integration with legacy SSO solutions such as CA SSO and Oracle Access Manager
Use your Access Management solution as a complete Web Application Firewall and dynamically react to attack heuristics
Built-in web application and services for automated plugin registration allows application teams to self-register plugins
Integrations
Contact Us for Assistance
